Every day, everywhere you go, you see someone completely focused on his or her mobile phone, even when they are surrounded by friends and family.Why is this so? I’m not an expert in human psychology but I suspect it is because they feel satisfaction in being connected, always online and updated by accessing a multitude of information every minute of every day. For some, this access to information at their fingertips truly enables super powers – making them feel like they are the master of the universe!Wow - did you see those predictions of traffic growth?
If we take a closer look at the figures presented by Cisco in the Visual Networking Index 2016 Report, for the ‘Global Mobile Data Traffic Forecast Update 2010-2015’, we see a prediction of massive traffic growth like we’ve never seen before. The continual increase in the number of smart devices, the hunger for more data for all the new digital experiences available for mobile end-users, the hype in social networking and new ways to drive data traffic (IoT, OTT) are all pushing this exponential increase in mobile internet traffic.
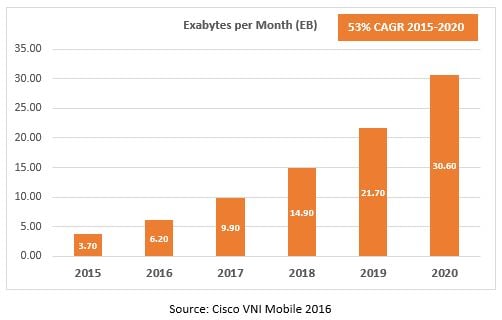
Although I hate to be the bearer of bad news, these growth forecasts are not as rosy as they seem. But please do not stop reading, because the most interesting part is coming next…
The risks of VoLTE
Although for mobile network operators (MNOs) this growth represents new revenue streams and a further increase to annual revenue per user (ARPU), they are under heavy pressure to keep up the pace and meet the extensive demands of an increasingly “connected lifestyle” for subscribers. Along with this, MNOs need to identify and quantify the risks that these new opportunities that “all you can eat” data brings.
One of the biggest risks, causing great concern for MNOs, is that these services grounded in the adoption of VoLTE technology (i.e. delivering superior quality of service (QoS) and high definition (HD) features) are opening breaches to new fraud threats.
Interestingly, most of these vulnerabilities are derived from the SS7 network environment concepts that have been repurposed for VoLTE. Moreover, since this technology lives in an all-data-IP-based network, the impact of intrusion may be even greater than in the legacy SS7-based networks. On top of this, it is important to highlight that VoLTE is even more exposed to fraud because signaling is implemented in the mobile OS instead of mobile-based broadband, as for 2G/3G telephony. This means that many of these vulnerabilities can actually be exploited remotely through mobile malware.
In order for MNOs to keep profit margins intact and manage massive volumes of data, they need to develop strategies to help them proactively arm their network against fraud attacks and close the holes left open by the packet-switch networks and all its SS7/SIP fragilities.
Types of fraud in VoLTE, and how to deal with them
The most common types of fraud faced in VoLTE are related to charging bypass, call spoofing, mobile malware, and call reselling, IRSF and Wangiri. Fraudsters are always trying new techniques to bypass MNOs’ controls and gain free access to services. This not only denies the operator of revenue, but also damages their reputation with subscribers and partners.
To cope with these new types of fraud in VoLTE technology, telco companies must adopt advanced fraud detection mechanisms. These systems must be capable of finding patterns of behavior that are different from the normal VoLTE subscriber, and be able to identify suspicious activities and/or fraud attempts no matter how they are perpetrated, regardless of the scheme used, or the origin/termination point of the fraud.
To address these key capabilities, leading Fraud Management Systems (FMS) use data mining models based on advanced statistical techniques to identify areas such as unusual behavior or subscribers with a high probability perpetrating fraud. The use of behavioral learning-based FMS are highly beneficial to increase the MNO’s knowledge on fraudsters’ behavior and generate potential fraud alerts.
Protecting VoLTE
For MNOs to support real-time data (voice) services, high volume and best-effort data in the same packet-switched domain, they will be burdened with huge capital and operating expenses from two separate networks. For most operators, VoLTE is the solution to this dilemma.
This real-time VoLTE environment needs to be supported by an advanced fraud management solution to effectively protect and monetize not only VoLTE calls, but all customer data traffic. New processes, controls and mechanisms are required for mobile operators to efficiently protect their network against fraud attacks, effectively mitigate risk, prevent revenue leakage and keep customers satisfied. Intelligent controls will enable MNOs’ operation teams to efficiently protect, detect, treat and analyze fraud.
As fraud is becoming more complex and harder to identify – early investigation and detection will be key to help MNOs tackle fraud faster, sharper and smarter. This will allow MNOs to better protect their network against the increasingly complex fraud schemas brought on by VoLTE.


Let Us Know What You Thought about this Post.
Put your Comment Below.